ESUPKG
Mass Deployment Guide for Jamf Pro
Jamf Pro administrators can take full advantage of Enterprise Software Update PKG Edition (ESUPKG) by quieting any distracting prompts and guiding users to update their Mac whenever it makes sense for the organization.
Table of Contents
Restrictions
Apple Software Update Preferences
Managed Login Items
Deploy ESUPKG via Self Service Policy
Deploy ESUPKG via Mass Deployment Policy with User Deferral
(Recommended) Jamf Recon at Startup
Appendix I: A Note on Scoping
Appendix II: A Note on Colliding Apple Software Update Methods
Configuration Profiles
Restrictions
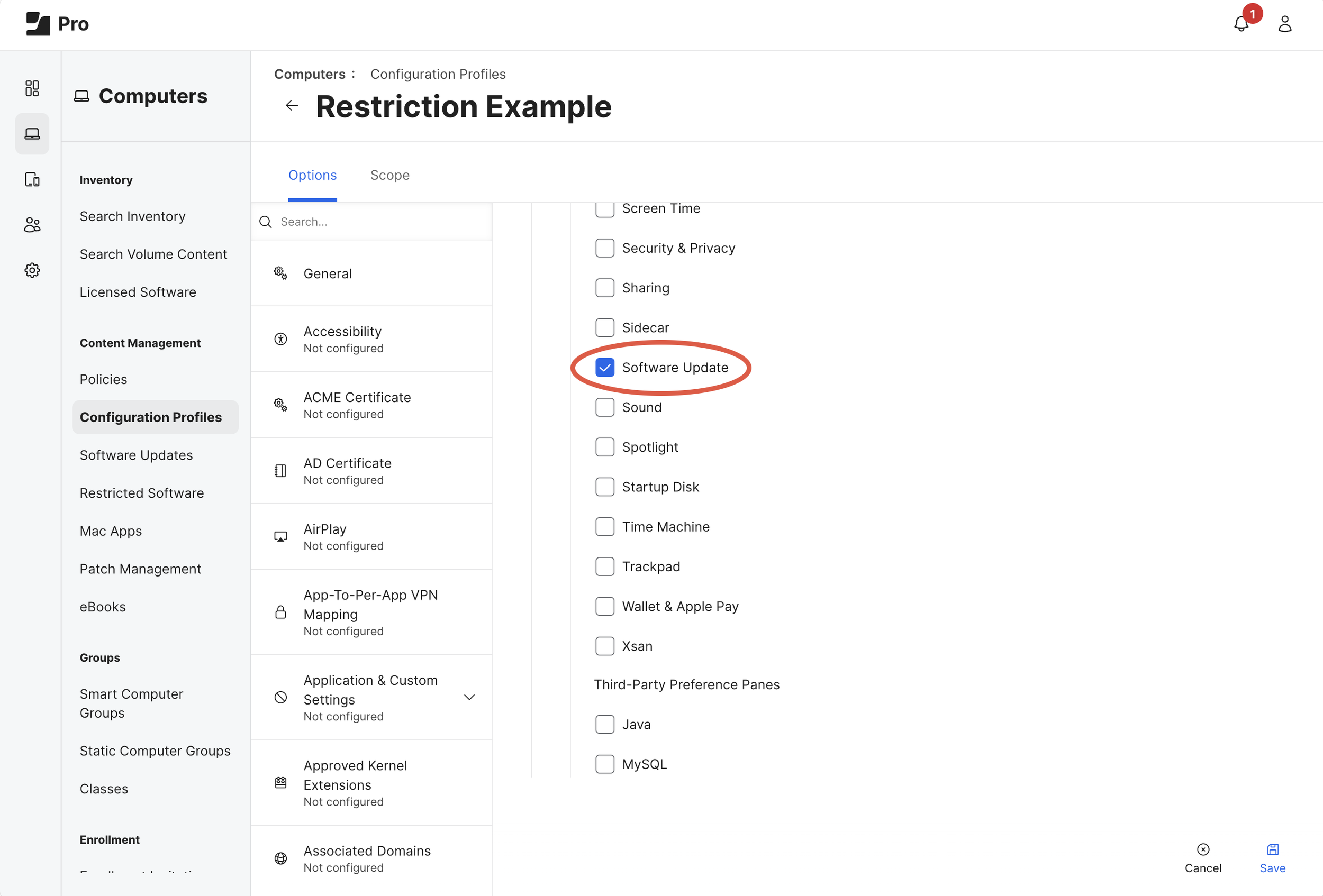
There are many methods of installing and updating macOS. Use restrictions to silence UX that may compete for user attention.
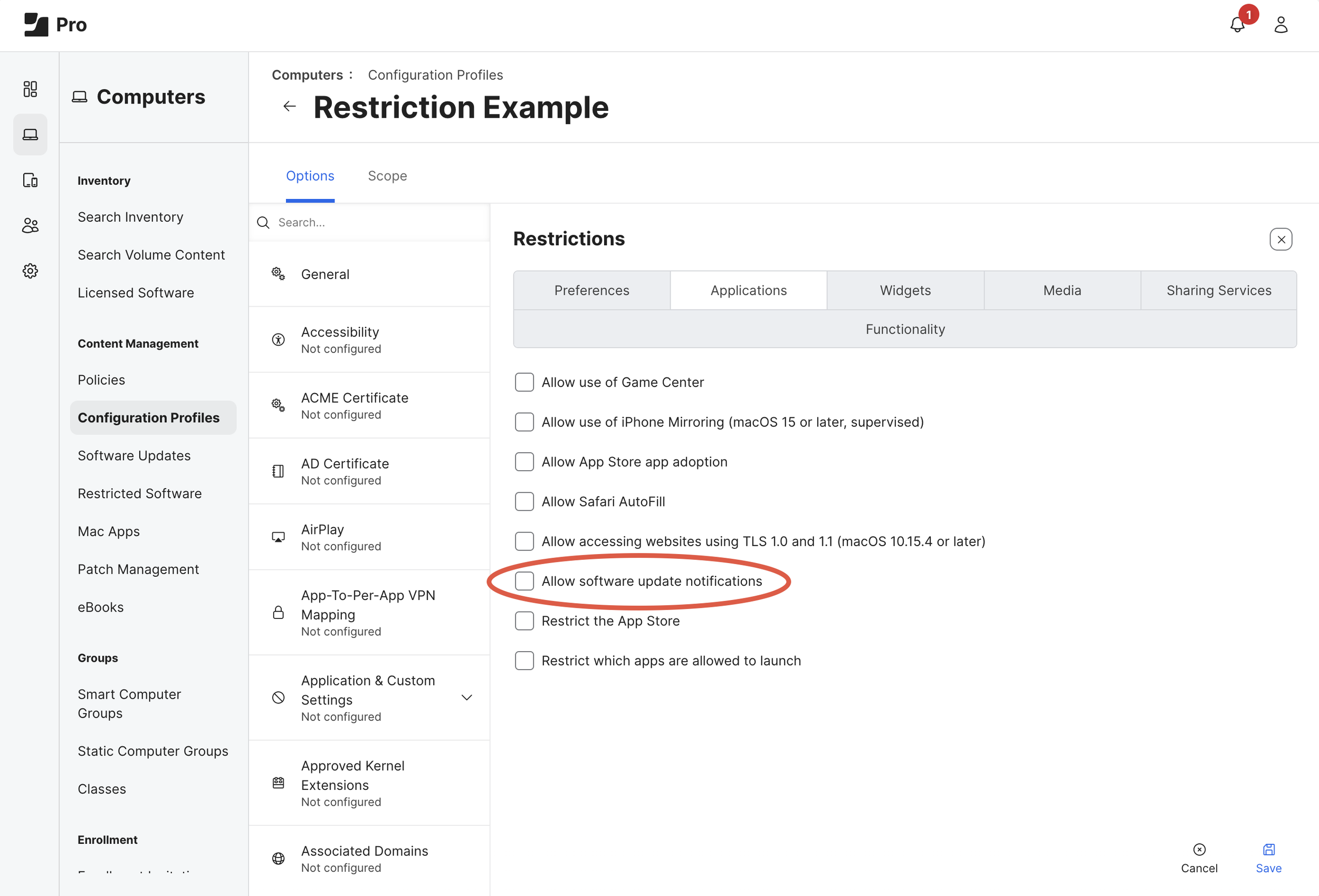
Create or Edit a macOS Configuration Profile (Computers > Configuration Profiles) with a Restrictions Payload (as shown below) to enforce the following preferences:
Preferences > Disable the Software Update item
Applications > Disable (uncheck) Allow software update notifications
(Optional) Functionality > Enforce macOS Software Update Deferral
*Note: only one of these Jamf Pro Restrictions Payloads should be applied to any single Mac.
Apple Software Update
Create or Edit a macOS Configuration Profile (Computers > Configuration Profiles) with a Software Update Payload (as shown below) to enforce the following preferences:
Disable (uncheck) Allow installation of macOS beta releases
Disable (uncheck) Automatically install macOS updates
Enable Automatically check for updates
note: this is automatic check is required for the below preferences to apply, which maintain current definitions for Apple’s XProtect and related security features.Enable Automatically install configuration data
Enable Automatically install system data files and security updates
Managed Login Items
Create or Edit a macOS Configuration Profile (Computers > Configuration Profiles) with a Managed Login Items Payload (as shown below) to allow the Floating Orchard Inc. Apple Developer Certificate Team Identifier:
Rule type: Team Identifier
Rule value: NFR6QTJLHZ
Rule comment: Floating Orchard Inc.
Patch Management Software Titles
Jamf Pro provides Patch Management Software Titles for each major version of macOS, as well as a combined definition. Using these inventory attributes can help with reporting on patch compliance, as well as enforcing updates across various macOS versions.
While the latest Apple security features can be found in the latest Apple hardware and OSs, stability improvements and security fixes (e.g. CVE and zero day exploits) are resolved across multiple recent major versions of macOS concurrently. On average, major versions of macOS have received these fixes from Apple for 2.5-3 years after initial release. ESUPKG will automate macOS updates for macOS 12 and newer, including releases no longer maintained by Apple, as long as the updates remain available on Apple’s Software Update servers.
Create New definitions (Computers > Patch Management) for any major versions of macOS you wish to maintain, as shown below.
Smart Computer Groups
Collection - Needs macOS Updates
Create a New Smart Computer Group (Computers > Smart Computer Groups) with the name Collection - Needs macOS Updates. In the below example, we’ll use the previously added Patch Reporting Software Titles for macOS to only include Macs needing minor and mainenance updates. As Macs install these updates, they will leave this Smart Group. This enables administators to practice change management within their environment by only making ESUPKG available when the organization is ready to support the newest macOS minor updates.
Note: If any Apple Software Update Deferral is in place (e.g. the Restrictions payload above), ensure your Macs become eligible for the specific versions defined in these Smart Groups before enforcing any ESUPKG deployment.
Policies
ESUPKG is designed to run Apple Software Updates on demand, whenever the ESUPKG .pkg file is invoked via Apple’s installer binary. Jamf Pro deploys .pkg files using Policies, and Jamf Pro administrators must make their own determinations about when, how frequently, and to whom they deploy macOS updates, as the process interrupts end users and prevents them from using their Macs for the duration of the update process.
Here we provide two examples of how to deploy ESUPKG via Jamf Pro policy: at the user’s convenience via Self Service Policy, and via Mass Deployment Policy with user deferral. We also provide an example of how to perform a Jamf Recon at Startup to detect newly-compliant Macs.
via Self Service Policy
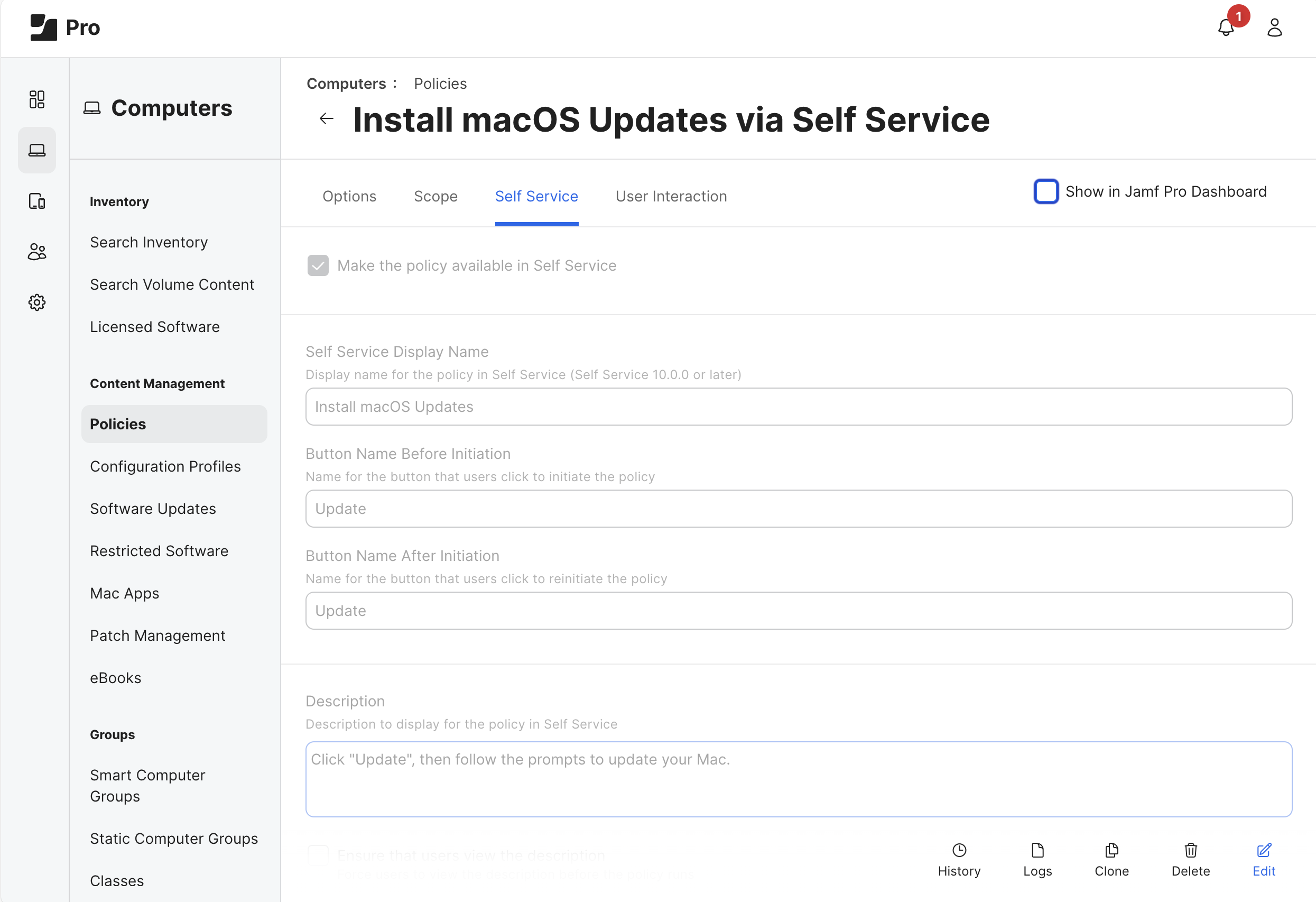
Create a New Policy (Computers > Policies) with the name Update macOS via Self Service. In the below example, we’ll use the previously created Smart Group as a basic Scope for when to offer the macOS Update to end users.
Options
General
Display Name: Update macOS via Self Service
Trigger: (none)
Frequency: Ongoing
Packages
Add the latest version of ESUPKG
(refer to Jamf Pro documentation on uploading packages)
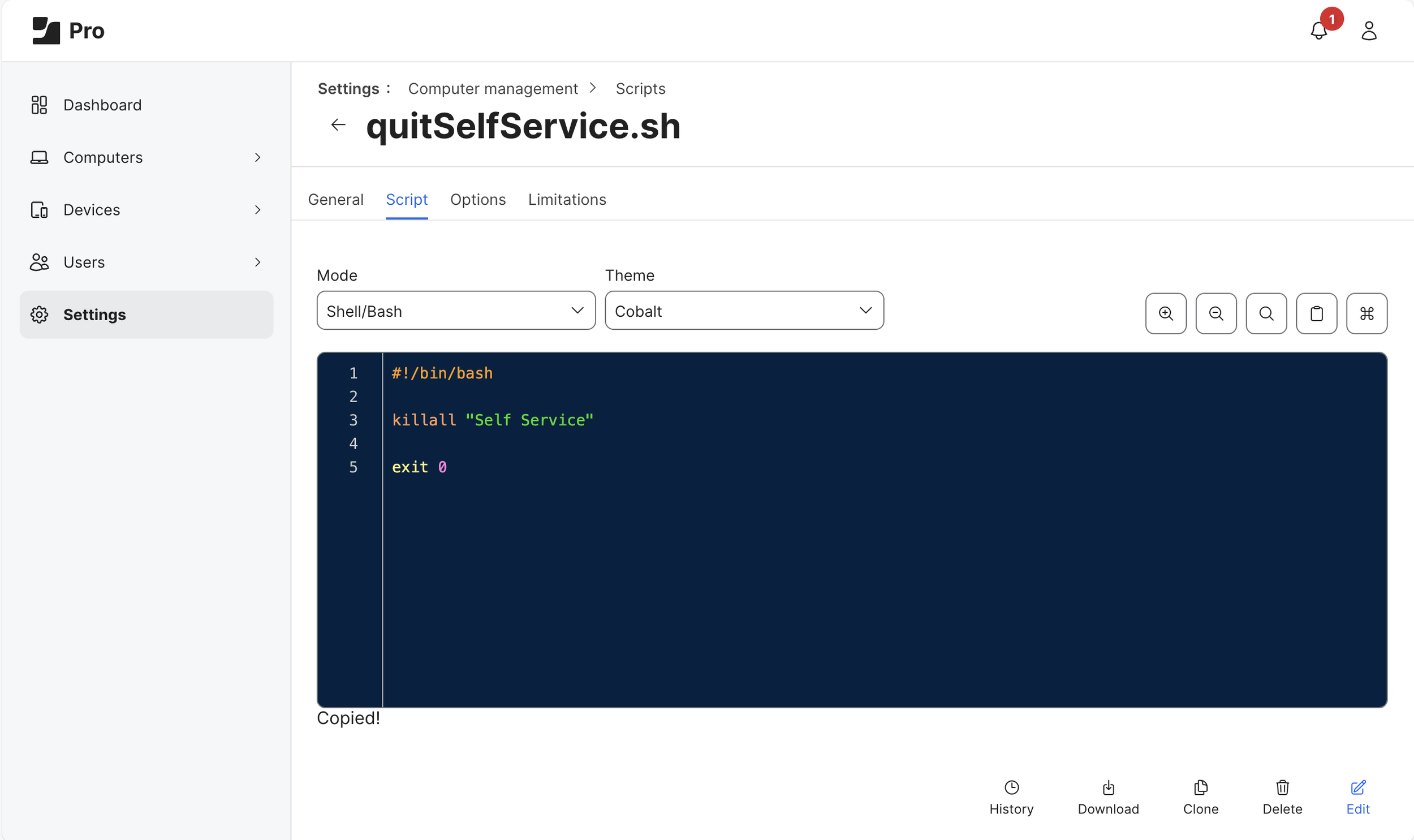
(Optional) Scripts
Add a script to quit Self Service.app (killall “Self Service”) before the process begins.
Scope
Specific Computers
Target: Collection - Needs macOS Updates
Self Service
Enable Make the policy available in Self Service
Customize the Title, Button Names, Description, Icon, and Category Display Preferences according to the needs of your organization
via Mass Deployment Policy
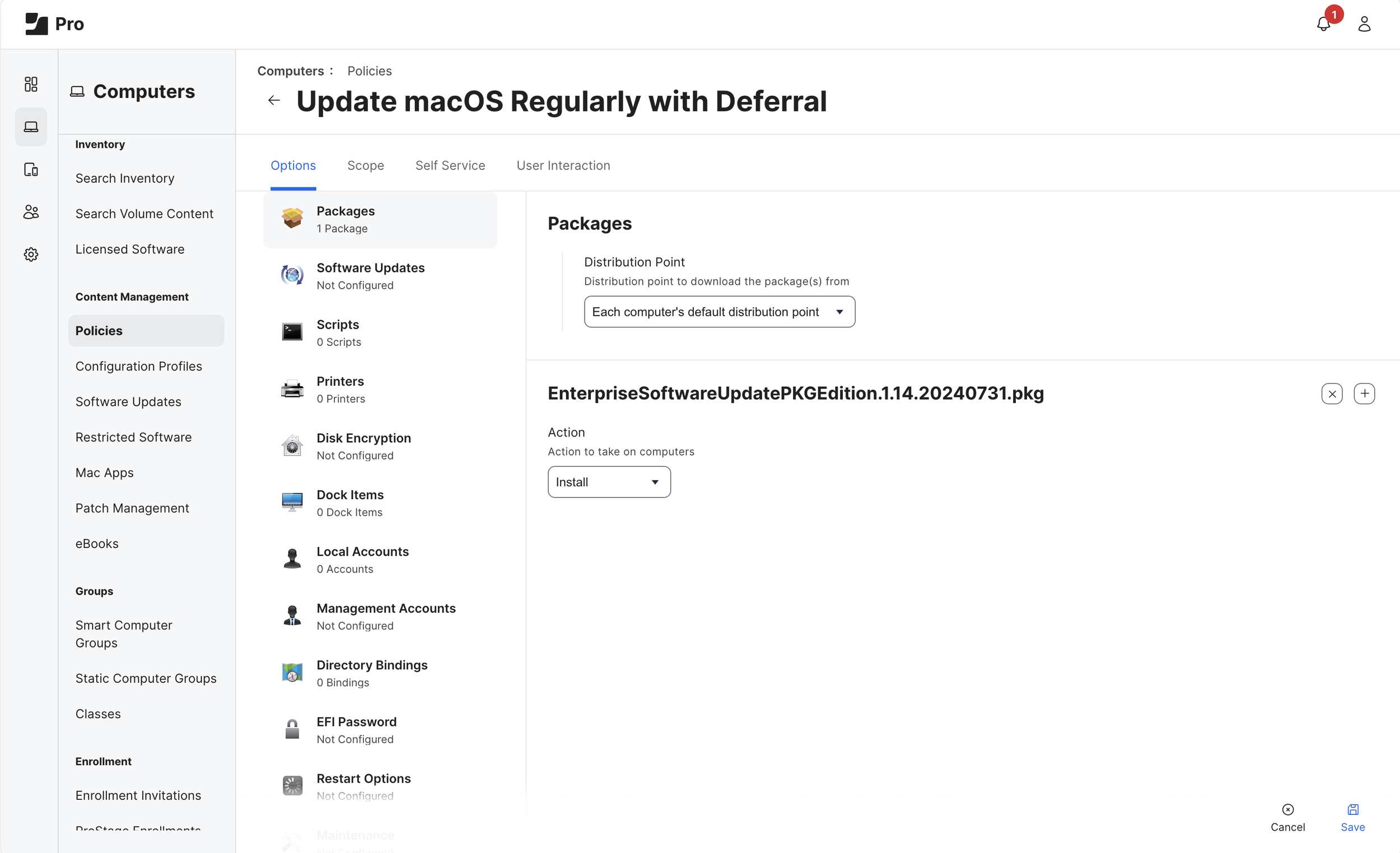
Create a New Policy (Computers > Policies) with the name Update macOS Regularly with Deferral. In the below example, we’ll use the previously created Smart Group as a basic Scope for when to prompt end users to update macOS.
Options
General
Display Name: Update macOS Regularly with Deferral
Trigger: Recurring Check-in
Frequency: Once Every Day
Packages
Add the latest version of ESUPKG
(refer to Jamf Pro documentation on uploading packages)
Scope
Specific Computers
(Example) Target: Collection - Needs macOS Updates
User Interaction
Enable a Deferral Type of Duration or Date
(Recommended) Jamf Recon at Startup
A simple Jamf Policy deployment of ESUPKG will report “Completed” in the policy logs before the ESUPKG service completes its own workflow of downloading and installing macOS updates. The policy examples above notably do not include an “Update Inventory” command (aka Jamf Recon) because the change we intend to make won’t be complete until after the Mac restarts.
One option for detecting this change as quickly as possible is to create a dedicated Jamf Recon policy, triggered at startup, but only scoped to Macs needing macOS updates. In this way compliant Macs will enjoy a faster startup experience.
Create a New Policy (Computers > Policies) with the name Check for Installed macOS updates at Startup. In the below example, we’ll use the previously created Smart Group as a basic Scope.
Options
General
Display Name: Check for Installed macOS updates at Startup
Trigger: Startup
Frequency: Ongoing
Maintenance
Check the Update Inventory checkbox
Scope
Specific Computers
(Example) Target: Collection - Needs macOS Updates
Appendix I: A Note on Scoping
Jamf Pro best practices depend heavily on good inventory data, which feeds the scoping that runs automation like Jamf Pro Policies. We provide the Self Service example policy because it avoids ‘sysadmin overreach’, which is historically a concern of Apple Inc.’s. Before mass-deploying ESUPKG beyond just Self Service, take time to build meaningful Smart Computer Groups, especially if different user groups or enrollment types deserve different experiences.
Seasoned Jamf Pro administrators (e.g. Certified 400-Level Jamf Pro Experts) will note how ESUPKG can be incorporated into a scripted workflow with additional end user considerations, and how comparatively incomplete our example Mass Deployment Policy is (above). Such skills and understanding are required to prevent Jamf Pro automation from colliding in complex environments; we therefore strongly encourage customers to introduce the tool via Self Service, and test any additional mass deployment workflows with a small pilot group.
For customers needing additional guidance, Floating Orchard Engineers are fully qualified to deliver Professional Services, building and supporting complex deployments Mac deployments.
Appendix II: A Note on Colliding Apple Software Update Methods
Jamf Pro and Apple macOS each offer multiple methods of configuring the mass deployment of macOS updates. Some of these methods include MDM prerequisites, which might only be met by a subset of enrolled Macs (e.g. Automated Device Enrollment). In these scenarios, entire categories of Macs not meeting these prerequisites may fail to update, lowering compliance outcomes in complex and larger environments.
Floating Orchard always encourages MDM enrollment according to Apple best practices, yet Enterprise Software Update PKG Edition is built to succeed without MDM prerequisites, empowering complex environments to achieve maximum macOS patching compliance even on Macs under minimal management. And for environments with no existing macOS update strategy, ESUPKG can immediately become a one-size-fits-all solution.
Before deploying ESUPKG in your environment, ensure any other methods of automating macOS updates are excluded through scoping, to avoid those methods colliding with the CLI method ESUPKG uses to deploy macOS Updates.
Of note, Jamf Pro’s own interface and features for deploying macOS Updates (Computers > Software Updates) leverages MDM commands with the aforementioned prerequisites. Admins should exclude Macs through scoping if they are being updated using ESUPKG instead.